Unveil the Power of SAML and How it Revolutionizes User Authentication
In our interconnected world, individuals often manage numerous applications, each with its own set of login credentials. This presents both users and organizations with security challenges. However, there is a robust solution available: Security Assertion Markup Language (SAML), providing a secure and convenient single sign-on (SSO) solution.
With SAML, users can access multiple applications using just one set of credentials, streamlining the authentication process and reducing the risk of password fatigue and security breaches.
SAML Components:
The Security Assertion Markup Language (SAML) establishes a secure and standardized approach to single sign-on (SSO) within a complex digital ecosystem. This framework relies on two critical entities: Identity Providers (IdPs) and Service Providers (SPs). Understanding their distinct roles is essential to appreciate the functionality and benefits of SAML.
Identity Provider (IdP):
The IdP functions as the authoritative source of user identities within a SAML environment. It shares similarities with highly secure central authentication systems, such as Azure Active Directory.
Key Responsibilities:
Centralized User Management: The IdP acts as a central repository for user identities. It securely stores and manages user credentials, including usernames, passwords, and potentially additional authentication factors like multi-factor authentication (MFA).
Authentication Authority: Users seeking access to services protected by SAML first authenticate with the IdP. The IdP verifies their credentials (username and password) through established login procedures. Upon successful verification, the user’s identity is confirmed.
Service Provider (SP):
The Service Provider represents the individual resources or applications that users seek to access. These services rely on SAML to communicate with the IdP for user authentication.
Key Responsibilities:
SAML Reliance: SPs rely on the SAML framework for user authentication. They do not directly manage user logins themselves, but instead, leverage the established communication protocol with the IdP.
Authorization Decisions: Once the user’s identity is confirmed by the IdP, the SP receives information about the user. This information might include attributes like department or role if provided by the IdP. Using this information in conjunction with its own access control policies, the SP determines whether to grant the user access to its resources.
Resource Access Management: Each SP manages access to its specific resources and functionalities based on the user’s authorization level.
IdP and SP Collaboration:

Implementing single sign-on for an organization should ensure that the service providers intended for support are SAML-enabled. This guarantees a seamless and secure SSO experience for users.
A SAML assertion, an XML document exchanged between an Identity Provider (IdP) and a Service Provider (SP), conveys user identity and authorization status. SAML assertions facilitate single sign-on, enabling users to access multiple applications with a single set of login credentials. They contain various user details, such as name, email address, roles, permissions, issuance time, and expiration time, along with a digital signature from the IdP to verify authenticity. This process involves users accessing a SAML-enabled SP.
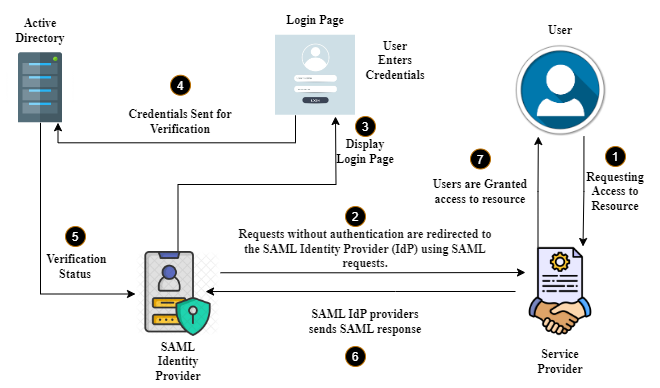
Working:
- The user accesses the Service Provider (SP) and is redirected to the Identity Provider (IdP) for authentication.
- Identity Provider (IdP) authenticates the user and generates a SAML assertion.
- SAML assertion is sent back to SP, which verifies its authenticity and grants user access.
- The user gains access to the requested resource without needing to log in again.
Conclusion:
Security Assertion Markup Language (SAML) stands as a powerful protocol for enabling secure and seamless Single Sign-On (SSO) experiences across various applications and services. By leveraging XML-based SAML assertions, organizations can streamline authentication processes, reduce password fatigue, and enhance overall security
Author: Sanghavi
